Zero Retries 0180
2024-11-29 — Canadian Amateur Radio Operators Experimenting with Encryption, APRS Radios, Utah Digital Comm. Conf., Raspberry Pi Compute Module 5 and Dev Kit… and a Case!, LILYGO T-TWR Plus
Zero Retries is an independent newsletter promoting technological innovation that is occurring in Amateur Radio, and Amateur Radio as (literally) a license to experiment with and learn about radio technology. Radios are computers - with antennas! Now in its fourth year of publication, with 2300+ subscribers.
About Zero Retries
Steve Stroh N8GNJ, Editor
Jack Stroh, Late Night Assistant Editor Emeritus
In this issue:
Canadian Amateur Radio Operators Experimenting with Encryption
Comments for This Issue (redirect to Comments page)
Web version of this issue - https://www.zeroretries.org/p/zero-retries-0180
Request To Send
Commentary by Editor Steve Stroh N8GNJ
Paid Subscribers Update
My thanks to John Alley K4UAE for upgrading from a free subscriber to Zero Retries to an Annual Paid Subscriber this past week!
K4UAE included this nice message with his paid subscription:
Thank you for this awesome forerunner / future looking perspective you have on Ham Radio!!! This is so awesome and refreshing to see and read!!! Reminds me of the thrill of those old Popular Electronics magazines arriving and thumbing through them all until the covers were wore out!! Keep it up!! I'm all in and playing with the higher speed packet here!!"
John - Thanks for the humbling favorable mention of Popular Electronics! PE was a formative influence of mine, especially the January 1975 issue that announced the Altair personal computer.
My thanks to Prefers to Remain Anonymous 58 for becoming an Annual Paid Subscriber to Zero Retries this past week!
Financial support from Zero Retries readers is a significant vote of support for the continued publication of Zero Retries.
Taking It a Bit Easy for Thanksgiving Holiday
My wonderful wife Tina convinced me to make this issue of Zero Retries a “light” issue in deference to this being a long holiday weekend here in the US and that we have our daughter, son-in-law, and their cats visiting and thus that should be a priority. Thus, Tina’s point is taken and I’ll defer the article Explaining the Use Case for Data Over Repeater - Part 2 that I had planned for this issue.
Have a great weekend, all of you co-conspirators in Zero Retries Interesting Amateur Radio activities!
Steve N8GNJ
Canadian Amateur Radio Operators Experimenting with Encryption
By Steve Stroh N8GNJ
Interesting development, and finally some progress in the common sense use of encryption in Amateur Radio - with an Amateur Radio twist.
Canadian Amateur Radio Operators Experimenting with Encryption
Codes and Encryption in Amateur Radio
Dave Goodwin, VE3KG – RAC Regulatory Affairs Officer
A small number of Canadian Amateurs are experimenting with encryption. Most of this experimentation is with some of the digital voice modes. Some of these experiments are on repeaters and some are on simplex frequencies – all in the Amateur VHF and UHF bands. A few experimenters have published their keys on obscure discussion boards on the internet, and a few have approached Innovation, Science and Economic Development Canada (ISED) for guidance on using encryption.
…
Here is what the International Telecommunication Union (ITU) Radio Regulations say on the subject:
“25.2A 1A) Transmissions between amateur stations of different countries shall not be encoded for the purpose of obscuring their meaning, except for control signals exchanged between earth command stations and space stations in the amateur-satellite service. (WRC-03)”
The ITU regulations raise the question of the purpose of a coding system: this regulation clearly says we “shall not” encode transmissions “for the purpose of obscuring their meaning.” So, your intentions count. Clearly, Amateurs may not make their communications unreadable by others. How can you encrypt without making your communication unreadable? By sharing the “key.”
Like Canada, FCC Amateur Radio regulations prohibit explicit obfuscation of transmissions:
§97.113 Prohibited transmissions.
(4) An amateur station transmitting a RTTY or data emission using a digital code specified in this paragraph may use any technique whose technical characteristics have been documented publicly, such as CLOVER, G‐TOR, or PacTOR, for the purpose of facilitating communications.
However, there are many ways that transmissions end up seemingly obfuscated, but without the specific intent to do so. One primary example is new data communications modes in Amateur Radio that require equivalent equipment or software to decode. One primary example is VARA HF and VARA FM, which implement a number of techniques such that only another station that’s running VARA can decode VARA transmissions.
But interestingly, §97.113 (4) names
CLOVER, G‐TOR, or PacTOR
… as
whose technical characteristics have been documented publicly
What’s interesting is that while there have been articles and other disclosures about how (for example) CLOVER was implemented, CLOVER remains a proprietary data mode only available in products from HAL Communications, and now Barrett Communications (who purchased HAL Communications).
Thus the same logic would seem to apply to newer data communications systems such as VARA (HF and FM) who have been “described” with some technical information, but are a proprietary product whose transmissions can only be received with another VARA station.
Ditto PACTOR 4.
In contrast to CLOVER, VARA, and PACTOR 4, a current example of a new data mode that’s implemented commendably well and “cleanly”, with no gray area about disclosing technical details is the new Improved Layer 2 Protocol (IL2P) which interleaves Forward Error Correction data into a AX.25 data transmission. That interleaving renders the transmission unreadable to those who aren’t set up to use IL2P, such as using an older AX.25 TNC to monitor transmissions on a channel used for packet radio.
Another gray area regarding encryption is the incidental use of encryption in Amateur Radio transmissions. For example, Amateur Radio microwave networks are often interconnected with the Internet for casual use of accessing websites or other systems on the Internet from an Amateur Radio station. It’s increasingly impossible, literally, to access some websites without using Hypertext Transfer Protocol Secure (HTTPS), which is end-to-end encryption between the browser software and the website. For example, trying to access the FCC website using “http://fcc.gov” is automatically redirected to “https://fcc.gov”. In my initial query of “Amateur Radio material” from the FCC website, specifically requesting an unencrypted communication, the FCC would not “honor my request” and required the use of encryption. Thus it’s impossible to access the fcc.gov website without the use of encryption.
Thus this development from Radio Amateurs of Canada (RAC) of blurring the lines of deliberate obfuscation / encryption with disclosure of the encryption key allowing decoding of the encryption, is interesting.
The most interesting aspect is that RAC has chosen to publish encryption keys used for encrypted transmissions used by Canadian Amateur Radio Operators in a central, public website, and doing so seems to make the use of encryption acceptable to Innovation, Science and Economic Development Canada (ISED) (Canada’s equivalent of the FCC).
Thus maybe there’s some hope for equivalent progress on the use of encryption here in the US. The issue of encryption for Amateur Radio transmissions is but one of many “needed modernizations” of the US Amateur Radio regulations. But like all suggested modernizations of FCC regulations, we have to be careful what we wish for and really think things through about requesting changes to regulations that we’ll have to live with likely for decades, given the slow pace of Amateur Radio regulatory changes in this era.
Publishing encryption keys would be another function of my imagined (currently fictional) Amateur Radio Standards Organization (ARSO) which would also be the Amateur Radio equivalent of the Internet Engineering Task Force (IETF) in collecting, arbitrating, and publishing technical specifications of new systems, and changes to old systems.
My thanks to Larry Gadallah NM7A and Randy Neals W3RWN / VE3RWN for bringing this Zero Retries Interesting development to my attention.
ZR > BEACON
By Steve Stroh N8GNJ
Short mentions of Zero Retries Interesting items.
Zero Retries Interesting Christmas Gift Suggestions
New Paid Annual Subscriber John Alley K4UAE’s mention of Popular Electronics triggered a memory to suggest these two wonderful series of books for Young Adult Techies. I loved them when I read them as a youth, and re-read them when they were brought back into print. These are personal recommendations - I won’t receive a a referral fee. Both sets of books are a wonderful nostalgic read for those like me who grew up and were interested in electronics in the 1960s and early 1970s. No microprocessors, computers, or mobile phones in these stories, and Amateur Radio does make occasional appearances in both series.
Carl & Jerry - Their Complete Adventures by John T. Frye W9EGV, Volumes 1 - 5. Carl & Jerry was a long running series of fiction stories in Popular Electronics from 1954 to 1964. Carl & Jerry were two teenage techies who got into various adventures either instigated by, or resolved by application of electronics. Credit for excerpting the Carl & Jerry stories out of Popular Electronics (which of course is now online for free reading) goes to Jeff Duntemann K7JPD who secured permission from Frye’s heirs to republish them as a compilation books. Available via Amazon (link is to Volume 5).
The Mad Scientists’ Club, by Bertrand R. Brinley and Charles Geer, Books 1-4. TMSC Book 1 and Book 2 are a compilation of a series of fiction stories in Boy’s Life Magazine. Book 3 - The Big Kerplop! and Book 4 - A Big Chunk of Ice: The Last Known Adventure of the Mad Scientists' were caught in an unfortunate downturn of the original publisher. The Big Kerplop! was long out of print, and A Big Chunk of Ice was an unpublished manuscript until Brinley’s son Sheridan Brinley found a friendly publisher to bring all of TMSC stories back into print. Available via Amazon (link is to a one-book compilation).
APRS Radios
John Langner WB2OSZ article on the How APRS Works blog:
Thanks to Jay DV7GDL for compiling this list of radios with APRS capability builtin.
APRS Radios (and other hardware) as of November 2024
(All radios can send and receive APRS text messages in addition to beacons and have user-accessible TNCs unless otherwise stated.)
This is a a good list, or a good start on the various radios that incorporate various APRS functionality directly in the radio and / or external APRS functionality via connection to an external device like a mobile phone / tablet. This list doesn’t mention the various DMR radios that have “APRS over DMR” capability (which, admittedly, may be out of scope).
In my opinion, this needs to be a web page so that it can be easily updated. Then, major updates of such a page could then be mentioned in periodic How APRS Works blog posts.
It takes a while to get the concept(s) across for APRS functionality built into a radio or a radio with “hooks” for APRS. For example, any implementation of packet radio functionality that incorporates DIRE WOLF (which is primarily authored by WB2OSZ) has excellent APRS capability, and thus systems such as DigiPi that prominently include DIRE WOLF as one of their built-in options, should be included in such a list.
Utah Digital Communications Conference 2025-02-22
Bridging the Gap: Effective Communication in Emergencies
Utah DCC and the Utah VHF Society have teamed up again to bring you the 8th Annual Utah Digital Communications Conference, held on Saturday, February 22nd, 2025, at the Salt Lake Community College Miller Campus in Sandy, Utah. This is a great one-day event to learn about digital modes and more about the Amateur radio hobby. We hope you will be able to attend.
Call For Proposals
Our volunteer presenters are the key to a successful event. We are now accepting presenter applications for the 2025 conference. We have seen the valuable impact of the amateur radio service during the recent disasters. This year, we will focus on emergency communications preparedness interests. We are open to all interests in amateur radio, digital communications, ARES, and EMCOM.
For questions, contact: utahdcc@gmail.com.
UDCC 2025 would be a unique conference if the focus were to be on digital (especially data) communications used in Amateur Radio Emergency Communications, such as the use of AREDN, Winlink, VARA FM (for fast transmission of data), integration of Starlink, Meshtastic, etc.
Raspberry Pi Compute Module 5 and Development Kit… and a Case!
Raspberry Pi Cofounder Eben Upton:
Today we’re happy to announce the much-anticipated launch of Raspberry Pi Compute Module 5, the modular version of our flagship Raspberry Pi 5 single-board computer, priced from just $45.
…
Compute Modules make it easier than ever for embedded customers to build custom products which benefit from our enormous investments in the Raspberry Pi hardware and software platform. Every subsequent generation of Raspberry Pi, except for Raspberry Pi 2, has spawned a Compute Module derivative. And today, we’re happy to announce the launch of Compute Module 5, the modular version of our flagship Raspberry Pi 5 SBC.
Meet Compute Module 5
Compute Module 5 gives you everything you love about Raspberry Pi 5, but in a smaller package:
A 2.4GHz quad-core 64-bit Arm Cortex-A76 CPU
A VideoCore VII GPU, supporting OpenGL ES 3.1 and Vulkan 1.3
Dual 4Kp60 HDMI® display output
A 4Kp60 HEVC decoder
Optional dual-band 802.11ac Wi-Fi® and Bluetooth 5.0
2 × USB 3.0 interfaces, supporting simultaneous 5Gbps operation
Gigabit Ethernet, with IEEE 1588 support
2 × 4-lane MIPI camera/display transceivers
A PCIe 2.0 x1 interface for fast peripherals
30 GPIOs, supporting 1.8V or 3.3V operation
A rich selection of peripherals (UART, SPI, I2C, I2S, SDIO, and PWM)
It is available with 2GB, 4GB, or 8GB of LPDDR4X-4267 SDRAM, and with 16GB, 32GB, or 64GB of MLC eMMC non-volatile memory. 16GB SDRAM variants are expected to follow in 2025.
The capabilities of this module are staggering, and it’s a drop-in replacement for the Raspberry Pi Compute Module 4, and doing so provides an immediate 2-3x performance increase.
While the Compute Module 5 (CM5) is not the most capable such computer in this form factor, long-time Raspberry Pi independent expert Jeff Geerling points out (and regularly tests this statement) that whatever Raspberry Pi units lack in bleeding edge performance and hardware capabilities, Raspberry Pi’s direct support, third party manufacturer support, and the ecosystem of users more than compensates for any “trailing edge” performance issues.
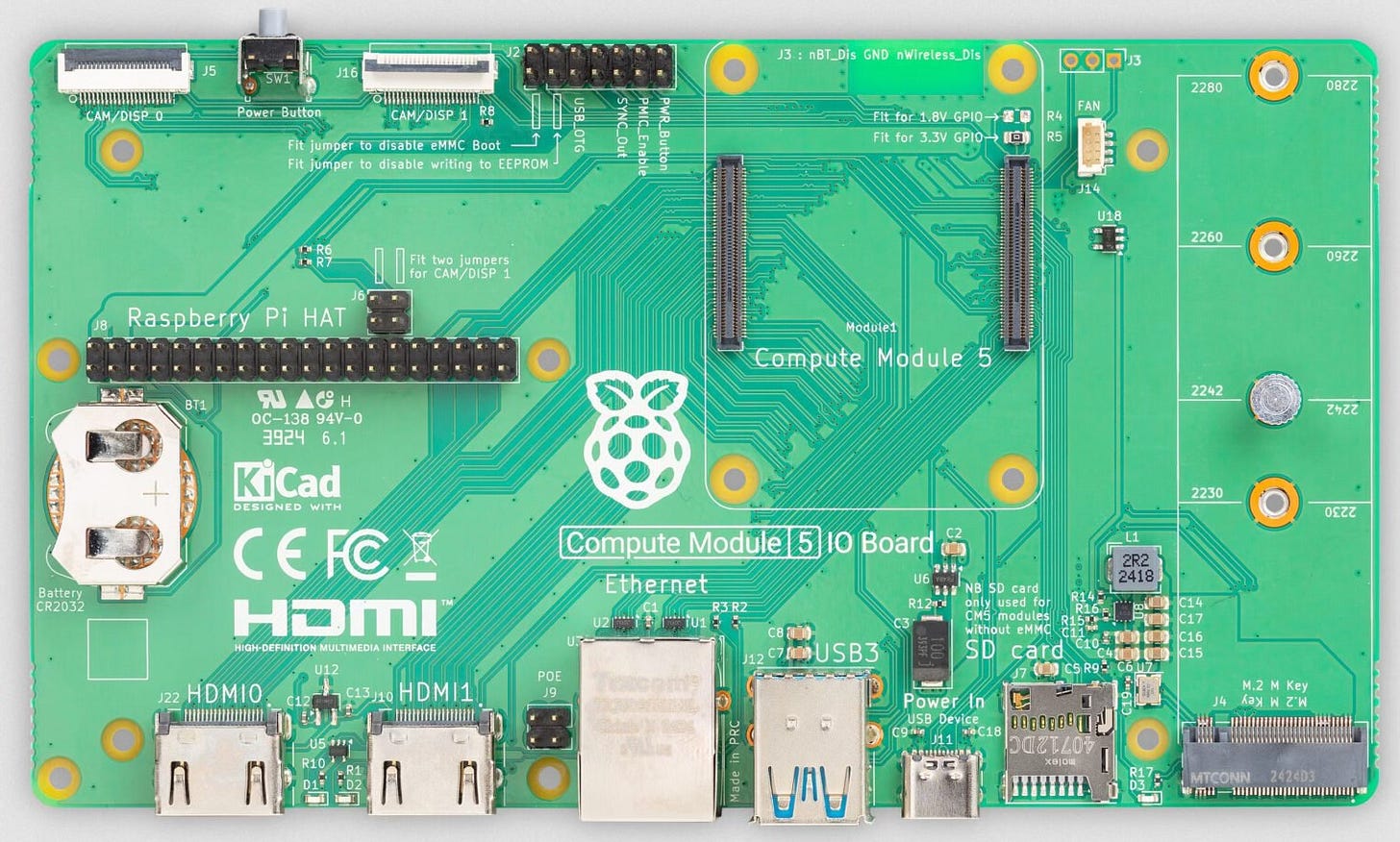
Raspberry Pi has offered “IO Boards” for some previous Compute Modules, so it’s not breaking any ground to do so with the CM51:
The Raspberry Pi Compute Module 5 IO Board breaks out every interface from a Compute Module 5. It serves both as a development platform and as reference baseboard (with design files in KiCad format), reducing the time to market for your Compute Module 5-based designs.
But what I don’t recall Raspberry Pi doing previously is to offer a case for the Raspberry Pi Compute Module IO Board as they have done for the CM5:
That is a handsome case. The lack of the other two USB connectors present on the Raspberry Pi 5 is nicely offset with the inclusion of two full size HDMI connectors - no Micro HDMI adapter cables needed!
The one criticism I have with the case is that although the CM5 I/O Board has a header for a Raspberry Pi HAT, if you want to route a cable from a HAT outside the case, this case makes no provision for doing so.
But that’s a minor quibble - note the KiCad label on the I/O Board. That’s there to signify that Raspberry Pi makes the KiCad files of the CM5 I/O Board available as open source so you can easily modify the design for specific requirements.
Not to mention that there are many, many Compute Module “carrier” boards available for Raspberry Pi Compute Modules.
I hope that some Amateur Radio manufacturer2 adapts the Compute Module 5 for their data communications system that runs the modem software on the unit… let’s just call it a “Smart Modem”. It’s easy to imagine running DIRE WOLF on this unit, thus perhaps called such a packaged unit the “DIRE WOLF TNC”.
Lastly, Raspberry Pi has amply demonstrated their commitment to industrial customers (especially continuing support for their oldest products) and thus the CM5, will have a “commercially long” lifetime. Thus I think that a radio / modem manufacturer deciding to use the CM5 is a good long term “bet” on good computing hardware… and the CM5 is much, much better than trying to do their own computing hardware or their own unique operating system.
LILYGO T-TWR Plus VHF and UHF “Amateur” Radios
For IoT projects, navigation and geolocation, emergency situations
T-TWR Plus is the ultimate development board for ambitious tech-enthusiasts. This board can achieve Walkie-Talkie functionality With integrated Wi-Fi, Bluetooth, and a SA868 Wireless Transceiver.
It also includes an OLED Display and GPS for precise location tracking. Unleash the potential of T-TWR Plus and make your tech dreams come true.
Currently, openrtx only supports version 2.0, not 2.1.
This unit has a lot of omissions that need to be addressed to make this into a usable radio for use in Amateur Radio, but you can see the potential (Wi-Fi, Bluetooth), especially its price point < US$65 and applicability for use with OpenRTX which supports M17. Eventually some manufacturer is going to strike the right balance between openness for open source software hacking and hardware completeness that enable more capabilities than the current commercial portable (or eventually, mobile / base) radios and open source hacking to make this better than commercial units. For an example, see the OpenWRT project for Wi-Fi access points, which AREDN is based on.
My thanks to friend Steve Monsey N0FPF for mentioning this to me.
Insightful Comments on Zero Retries 0179 - Erasure Codes, Multimode Repeater Experience, and Easier Block Diagramming
Louis Mamakos commented about Erasure Codes re: my mention of flamp:
Just a thought on multicast file distribution systems. There is a class of algorithms called erasure codes that take some chunk of data, run a transformation on it to break it up into blocks (the total size somewhat more than original.) Then a receiver need only receive K out of N blocks that were produced by the encoding algorithm to compute the original data. This sort of thing is used at small scale with Reed-Solomon coding and at large scale for storing files. Professionally, we used a product like this which would ingest files, generate blocks that were then stored at multiple geographically dispersed locations. By tuning K and N, you would get disaster recovery and the system overall in managing all the metadata was very scalable.
The application for amateur radio beacons and the like is to just transmit blocks and the receiver can start receiving them at any time and eventually reconstruct the original object. Some research reveals some commercial work for such a thing to be deployed on unidirectional broadcast satellite links where a reverse channel to ask for "fills" wasn't available. Missing a block means you don't have to wait for that one block to be retransmitted to you much later; you might still reconstruct the object sooner.
There appear to be some open-source libraries to do this encoding and decoding computation and that would then need a UI and data transport interface wrapped around it. This sounds like a great opportunity for combine ham radio and thesis work for the right person :-)
Really enjoy Zero Retries, thanks!
Tony Langdon commented about his experience with multimode repeaters re: my discussion of multimode repeaters:
As someone who has experimented with multimode repeaters and hotspots for years, I do see a lot of potential for adding data capabilities to FM repeaters. I already have a test system running 5 modes using a MMDVM (currently on a dummy load until I get an antenna up and the paperwork sorted). The system cleanly switches modes, and having data modes alongside the voice modes (including FM) would be neat.
I also have extreme demands on VHF/UHF antennas from monitoring multiple frequencies to supporting APRS and intending to run some sort of data service. Being able to aggregate data services, including repeaters that can receive data such as APRS payloads over M17 or MMDVM-TNC, while transmitting traffic from remote Internet stations would be neat.
An additional factor here is the terrain lends itself to a lot of "hidden station" issues on simplex, which duplex should mitigate, especially when the repeater output isn't tied up with other traffic..
Lots of experimentation ahead, and I'm looking forward to having a play.
Winston Lawrence KD2WLL commented about his technique for easily creating block diagrams with help from AI re: my frustration with no easy way to create diagrams:
I read through this article quickly, "Explaining the Use Case for Data Over Repeater - Part 1." I will have to go back and reread it as there is a lot of information, and I particularly want to re-read your comments on FLDIGI and FLRAMP for a project that I have in mind. However, one of your comments stood out
"All of this would be much easier explained in an interactive block diagram, which I intend to do eventually. I have not yet spent time learning how to instruct an AI like ChatGPT to create such diagrams, even videos, but that’s on my long to-do list."
I wrote a post on doing this
https://kd2wll.winstonlawrence.us/radios_and_technology/ai_and_amateur_radio_applications.html (direct link because it's still draft).
My thanks to Louis, Tony, and Winston for their insightful comments from their hands-on experience with the subjects that I wrote about (from no hands-on experience). The brain trust, knowledge base, and hands-on experience in Zero Retries Interesting areas that has self-assembled around Zero Retries is really amazing. I’m looking forward to more exchanges like this in 2025, but a bit more realtime including regular videoconferences and an email list dedicated to Zero Retries feedback and extended discussion.
Feedback on the VGC VR N76 and BTECH UV-PRO APRS Capabilities
Georges Auberger WH6AZ on the Radiomail email list:
I don't know about the N75, but I've been testing the beta firmware v 0.7.10-1 on VGC VR-N76 and the BTECH UV-PRO.
While the KISS TNC is now accessible via the BLE specification and therefore available in RadioMail, I've experienced performance problems.
Mainly, the radio has a hard time decoding back-to-back frames, which are common in AX.25 connection-oriented mode like used for Winlink. This means that as the frames are lost, it leads to a lot of unnecessary retransmissions to complete a session.
Prior to this latest update, the transmission also had issues but now seems to be able to keep up better, so it seems that they are making incremental improvements.
I'm in touch with the firmware developer and have been providing feedback along the way. It's encouraging to see they are making progress.
My sense is that we’re in an awkward era bridging between pure hardware radios (RF hardware with permanently fixed functionality) and fully software defined radios where the hardware is essentially Digital to Analog and Analog to Digital converters, with some “still necessary” hardware like power amplifiers and filters.
Like the issues with LILYGO T-TWR Plus mentioned in an earlier article, the radio manufacturers still think that they’re in the “radio hardware” business instead of the “computers - with antennas” business. As such, they continue to manufacture mostly hardware radios enhanced with some software-defined add-on functionality, and so we keep having nagging issues like this that can only be partially addressed with software updates.
Once we do get to full software defined radios / transceivers, these awkward issues just go away - software updates can fix such issues at a much lower level for much improved functionality. We’re getting there, gradually.
We’re agonizingly close to full Software Defined Radios for VHF / UHF and portable form factors - see the OpenHT. While that unit also has some issues (especially very low transmit power), that’s because it’s a prototype engineering project. You can see that those issues can be overcome with some additional engineering and development. We just need a manufacturer… or group… brave enough… visionary enough… with sufficient resources to step up and shepherd a project like the OpenHT through to completion.
44 NET Email Service 44.32.132.10
Mason Turner AF4MT on the ARDC Community email list:
I wanted to document my 44net email project. there is a basic web/email server running at
https://44.32.132.10
with a basic landing page where you are welcome to create an email account, please use your callsign as any other addresses will be deleted, so for example, af4mt@... .
Directions: Once on the landing page, you can select "Login Email" Or "Create Account". When creating an account ONLY ENTER YOUR CALLSIGN AND NOT A FULL EMAIL ADDRESS. To login you can either use just your callsign or the full address, so either "callsign@..." or "callsign" will work as the login for the webmail client.
The SMTP, POP3 and IMAP server information is listed on the landing page. I am currently waiting on a DNS delegation to attempt to add SPF, DMARC, DKIM, PTR etc. dns records.
OS: Win11
WebServer: Apache2/XMPP
SSL Certificate: ZeroSSL (They will issue free 90 day certificates, "Certify The Web" is a good GUI program to manage SSL certificates.)
Webmail Client: Rainloop
Email Server: hMailserver
Feel free to send me an email at af4mt @ 44net.email
Thank you,
Mason AF4MT
This is a pretty cool development for experimentation on 44Net! Kudos to AF4MT for stepping up and hosting this service for the benefit of us 44Net users.
Video on LongChat Data Mode
A new QRP digital chirp mode for Ham Radio.
LongChat is a QRP Ham Radio Text Chat Software that uses chirp signals for power efficient messaging. Chirp symbols with an audio bandwidth 300 Hz -2700 Hz are generated on the PC side for encoding the messages.
You may download the free LongChat software and the setup instructions at the location below:
https://drive.google.com/drive/folders/1NQwbeoHE3vPLORGN1krpSNHHI9brhDJh
You may read the article of Pieter-Tjerk de Boer at:
I first wrote about LongChat in Zero Retries 0157- LongChat - New QRP Digital Mode. Development of LongChat has proceeded since that initial mention 😆.
My thanks to Ren Roderick K7JB, Jeff Davis KE9V, Ron Thomas N4RT, Dan Romanchik KB6NU, and Amateur Radio Weekly Issue 357 for mentioning this video.
N4RT asked me if I knew of contact info for LongChat’s author, or where on the HF bands LongChat is being used, but I had no additional information. If you do know such info, please reply via email or in the comments for this issue.
NOSaprs IPV6 Support
Maiko Langelaar VE4KLM on the nos-bbs email list:
You can now connect to the APRS internet system over IPV6
Check out the development repo along with other stuff.
You won't see anything visibly different, it's just that internally, the code will now try to resolve the APRS IS server hostname in IPV6 first. If that does not work, it will just revert to the regular IP name lookup.
This link for “NOSaprs” is dated 2003, but I wasn’t able find any additional, more current information on NOSaprs.
Still, pretty cool that IPv6 capability is slowly creeping into Amateur Radio.
Pi-Pico RX - Breadboard Version
Dan Romanchik KB6NU on his KB6NU’s Ham Radio Blog:
There’s so much interesting stuff out there that I’m never going to get to it all. I blog about these projects, though, so that I don’t forget about them and to let others know about them. If you’v ever built or used one of these projects, please leave a comment below or email me directly.
Pico-based SDR runs stand-alone
Microcontrollers are getting to be very powerful. The Raspberry Pi Pico, for example, feature dual core processors, running at frequencies up to 150 MHz, with 520 kB of SRAM, and 4 MB of on-board flash memory. They’re very inexpensive, too. You can get one of these microcontrollers from reputable dealers for less than $8. If you’re willing to take a flyer on Ali Express, some of them are going for less than $2.
As shown in the video, this lets one build a software-defined radio (SDR) without a PC!
Think of the possibilities. One of the things that comes to my mind is to couple this with an Si5351 module and amplifier to make a small HF transceiver.
For more information:
Article discussing how it works.
Discussion on qrptech@groups.io.
Just too much good stuff that’s Zero Retires Interesting out there like this project.
Note that the current version of the Raspberry Pi Pico is the Raspberry Pi Pico 2 W. The “2” update was a significant increase in performance from the original Raspberry Pi Pico, and the just-announced “2 W” adds 2.4 GHz Wi-Fi and Bluetooth onboard the unit for a grand total of… US$7.
New Chinese Satellite Completes Frequency Coordination
ANS-329 AMSAT News Service Weekly Bulletins, by Mark Johns:
The satellite frequency coordination committee of the International Amateur Radio Union (IARU) on November 15 completed approval of frequency requests from the Chinese Amateur Satellite Group (CAMSAT) for a new amateur satellite to be launched next year.
CAS-11, a 6U CubeSat will include:
HF/UHF – H/U Mode Linear Transponder, with a bandwidth of 15kHz downlink centered at 435.505 MHz, EIRP 24 dBm
Uplink 21.320 MHz +/- 7.5 kHz.VHF/UHF – V/U Mode Linear Transponder, with a bandwidth of 30kHz downlink centered at 435.540 MHz, EIRP 24 dBm.
Uplink 145.860 MHz +/- 15 kHz.VHF/UHF – V/U Mode FM Transponder, downlink at 435.600 MHz, EIRP 24 dBm
Uplink at 145.925 MHzVHF/UHF – V/U Mode digital store-and-forward Transponder, downlink at 435.700 MHz, EIRP 24 dBm
Uplink at 145.895 MHzUHF – CW Telemetry Beacon and
UHF telemetry beacon using AX.25 4.8k/9.6kbps GMSK at 435.570 MHz, EIRP 23 dBm.
The above transponders and beacon will work 24/7 when the satellite power supply is sufficient. Amateur radio enthusiasts around the world can use it for two-way radio relay communication, data storage and forwarding communication, and receive satellite CW beacons.
The CAS-11 satellite will also be equipped with a 2.4 GHz multi-mode amateur radio satellite beacon transmitter, which is designed and built by university students, high school students and primary school students from Beijing Donggaodi Science and Technology Museum and Beijing University of Posts and Telecommunications under the guidance of CAMSAT. This is an unprecedented satellite project in China. It has brought opportunities for learning and practicing amateur radio and amateur satellites to students of all grades from elementary school to university, and promoted the application of amateur radio in space. This 2.4 GHz experimental beacon transmitter can switch to transmit five different modes of radio signals, and it will work continuously when the satellite is fully powered.
This project aims to cultivate students’ knowledge, skills and interests in amateur radio satellites. All transmission modes operate at 2.4 GHz, and the working modes are converted by the on-board computer program and ground remote control commands. It can work in the following modes: CW Telemetry Beacon, FT8 Telemetry Beacon, PPM Telemetry Beacon, or USB/SSTV Robot36, PD120 1. This beacon will transmit at 2405.500 MHz, EIRP 27 dBm.
CAS-11 carries three cameras, and the photos it takes are stored in the flash memory on the satellite. The builders have designed a simple remote control system based on DTMF commands. Amateur radio enthusiasts around the world can send DTMF commands to download the photo catalog and all photos taken by all cameras.
Anticipating a launch in September, 2025 into a 536 km polar orbit from Haiyang Sea Launch Platform, Shandong, China.
[ANS thanks IARU and Alan Kung, BA1DU, of CAMSAT for the above information.]
Notable in this announcement are the V/U Mode digital store-and-forward Transponder capability and the downlink on 2.4 GHz. It was also impressive that all the various radios will be in service simultaneously “when fully powered”. I’m looking forward to learning more about this satellite’s data capabilities.
Join the Fun on Amateur Radio
If you’re not yet licensed as an Amateur Radio Operator, and would like to join the fun by literally having a license to experiment with radio technology, check out
Join the Fun on Amateur Radio for some pointers.
Zero Retries Frequently Asked Questions (FAQs) — In development 2023-02.
Closing the Channel
In its mission to highlight technological innovation in Amateur Radio, promote Amateur Radio to techies as a literal license to experiment with radio technology, and make Amateur Radio more relevant to society in the 2020s and beyond, Zero Retries is published via email and web, and is available to everyone at no cost. Zero Retries is proud not to participate in the Amateur Radio Publishing Industrial Complex, which hides Amateur Radio content behind paywalls.
My ongoing Thanks to:
Tina Stroh KD7WSF for, well, everything!
Annual Founding Members who generously support Zero Retries financially:
Founding Member 0000 - Steven Davidson K3FZT (Renewed 2024)Founding Member 0001 - Randy Smith WU2S (Renewed 2024)
Founding Member 0002 - Chris Osburn KD7DVD (Renewed 2024)
Founding Member 0003 - Don Rotolo N2IRZ (Renewed 2024)
Founding Member 0004 - William Arcand W1WRA (Renewed 2024)
Founding Member 0006 - Todd Willey KQ4FID (Renewed 2024)
Founding Member 0007 - Merik Karman VK1DF / VK2MKZ (Renewed 2024 with two Founding Member subscriptions!)
Founding Member 0008 - Prefers to Remain Anonymous 14 (Renewed 2024)
Founding Member 0009 - Prefers to Remain Anonymous 19
Founding Member 0011 - Rick Prelinger W6XBE (New 2024)
Founding Member 0012 - Ryan Tolboom N2BP (New 2024)Numerous Annual and Monthly subscribers who also generously support Zero Retries financially!
Want to Support Zero Retries?
The most effective way to support Zero Retries is to simply mention Zero Retries to your co-conspirators that are also interested in knowing more about technological innovation that is occurring in Amateur Radio and encourage them to become a fellow subscriber.
One particularly effective method of promoting Zero Retries is to add a mention of Zero Retries to your QRZ page (or other web presence) and include a link:
If you’d like to financially support Zero Retries, becoming a paid subscriber is greatly appreciated and helps offset expenses incurred in publishing Zero Retries. Paid subscriptions for Zero Retries are entirely optional, as explained in this special issue of ZR:
Zero Retries Administrivia - Activating Payment Options.
These blogs and newsletters regularly feature Zero Retries Interesting content:
Dan Romanchik KB6NU mentions “Zero Retries Interesting” topics so regularly on his blog (that I otherwise wouldn’t know about) that I’ve bestowed on him the honorific of Pseudostaffer.
Jeff Davis KE9V also mentions “Zero Retries Interesting” topics so regularly on his blog (that I otherwise wouldn’t know about) that I’ve bestowed on him the honorific of Pseudostaffer.
Amateur Radio Weekly by Cale Mooth K4HCK is a weekly anthology of links to interesting Amateur Radio stories that often feature “Zero Retires Interesting” topics.
Experimental Radio News by Bennet Z. Kobb AK4AV discusses (in detail) Experimental (Part 5) licenses issued by the US FCC. It’s a must-read-now for me!
RTL-SDR Blog - Excellent coverage of Software Defined Radio units.
TAPR Packet Status Register has been published continuously since 1982.
Hot Iron - The Journal of the Constructor’s Club is a delightful quarterly newsletter.
Other Substack Amateur Radio newsletters recommended by Zero Retries.
These YouTube channels regularly feature Zero Retries Interesting content:
HB9BLA Wireless by Andreas Spiess HB9BLA
KM6LYW Radio by Craig Lamparter KM6LYW (home of the DigiPi project)
Modern Ham by Billy Penley KN4MKB
Tech Minds by Matthew Miller M0DQW
These podcasts regularly feature Zero Retries Interesting content:
Store and Forward - a podcast about the past and future of amateur radio, by Kay Savetz K6KJN (curator of the Digital Library of Amateur Radio and Communications) and Steve Stroh N8GNJ (Editor of Zero Retries).
Ham Radio Workbench by George Zafiropoulos KJ6VU (and friends)
Foundations of Amateur Radio by Onno Benschop VK6FLAB
If you’re reading this issue on the web and you’d like to see Zero Retries in your email Inbox every Friday afternoon, just click below to join 2200+ other subscribers:
Please tell your co-conspirators about Zero Retries — just click:
Offering feedback or comments for Zero Retries is equally easy — just click:
If you’re a fellow smart person that uses RSS, there is an RSS feed for Zero Retries.
Social Media:
Zero Retries (N8GNJ) is on Mastodon — n8gnj@mastodon.radio — just click:
Zero Retries (N8GNJ) is also on Bluesky — @n8gnj — just click:
Email issues of Zero Retries are “instrumented” by Substack to gather basic statistics about opens, clicking links, etc.
More bits from Steve Stroh N8GNJ:
SuperPacket blog — Discussing new generations of Amateur Radio Data Communications - beyond Packet Radio (a precursor to Zero Retries)
N8GNJ blog — Amateur Radio Station N8GNJ and the mad science experiments at N8GNJ Labs in Bellingham, Washington, USA
Thanks for reading!
Steve Stroh N8GNJ / WRPS598 (He / Him / His)
These bits were handcrafted (by a mere human, not an Artificial Intelligence bot) in beautiful Bellingham (The City of Subdued Excitement), Washington, USA, and linked to the Internet via Starlink Satellite Internet Access.
2024-11-29
Blanket permission is granted for Amateur Radio use of any Steve Stroh content in Zero Retries for Amateur Radio newsletters and distribution via Amateur Radio such as (but not limited to) Packet Radio Networks, Packet Radio Bulletin Board Systems, Repeater Nets, etc. Specific blanket permission is granted to TAPR to use any Steve Stroh content in Zero Retries for the TAPR Packet Status Register (PSR) newsletter (I owe them from way back).
In such usage, please provide appropriate authorship credit for the content.
If you’d like to republish an article in this issue for other uses, just ask.
All excerpts from other authors or organizations, including images, are intended to be fair use. Unless otherwise noted in the article, there are no paid promotional items in any Zero Retries articles.
Portions Copyright © 2021, 2022, 2023, and 2024 by Steven K. Stroh.
Footnotes for this Issue
Other than the very welcome addition of a hardware ON / OFF button 🤣
Yes, this is obviously a project that can be tackled by an individual or small group, but it would be so much cooler to have a manufacturer build this and support it as a turnkey product.




This matter was explained in an issue of CQ or CQ-VHF in the early 2000's before HSMM started using Mesh technology to restrict the connections to hams. There was a pre-defined key on the ARRL website. So the Canadian thing is the same sort of thing. As N8GNJ points out there really is no need to use encryption and using the ARES angle to allow it is pathetic since there are now so many ways to handle that kind of traffic outside of ham radio. It's important to remember the rules we have in the USA were crafted before digital was a thing. "Intentionally obscuring the meaning" was likely referring to mostly the use of coded lingo on voice. Even analog scrambing and like wasn't much of a thought at the time. And yes civilian encryption was prohibited within my life time. (I believe that changed during the Clinton administration)
Regarding encryption and publishing keys in a public location.. this makes me nervous and twitchy. I'm old enough to have lived through the "Clipper Chip" thing years ago, and various attempts by government to implement encrypted communication systems and methods which incorporate some "key escrow" element. The theory being that, in exchange for the government "allowing" you to use encryption systems in communications, the key available in the escrow mechanism would only be used by the government for "legitimate" purposes only.
All of this was with respect to proposed regulatory restrictions on encrypted content in the US on the Internet and in other communication systems, which is a little removed from the amateur radio service. My concern here is that some accomodation in the amateur radio service with "escrowed" or published keys might get pointed to as precedent or demonstration in an out of context way and used to shape policies for trusted communications across the Internet.
So I think if this is something that's adopted in the amateur radio service, it would be good to carefully consider the optics, labeling and description of such a system that conveys the narrow purpose and applicability. And not inadvertently be the camel's nose in the tent as far as encryption policy advocacy.